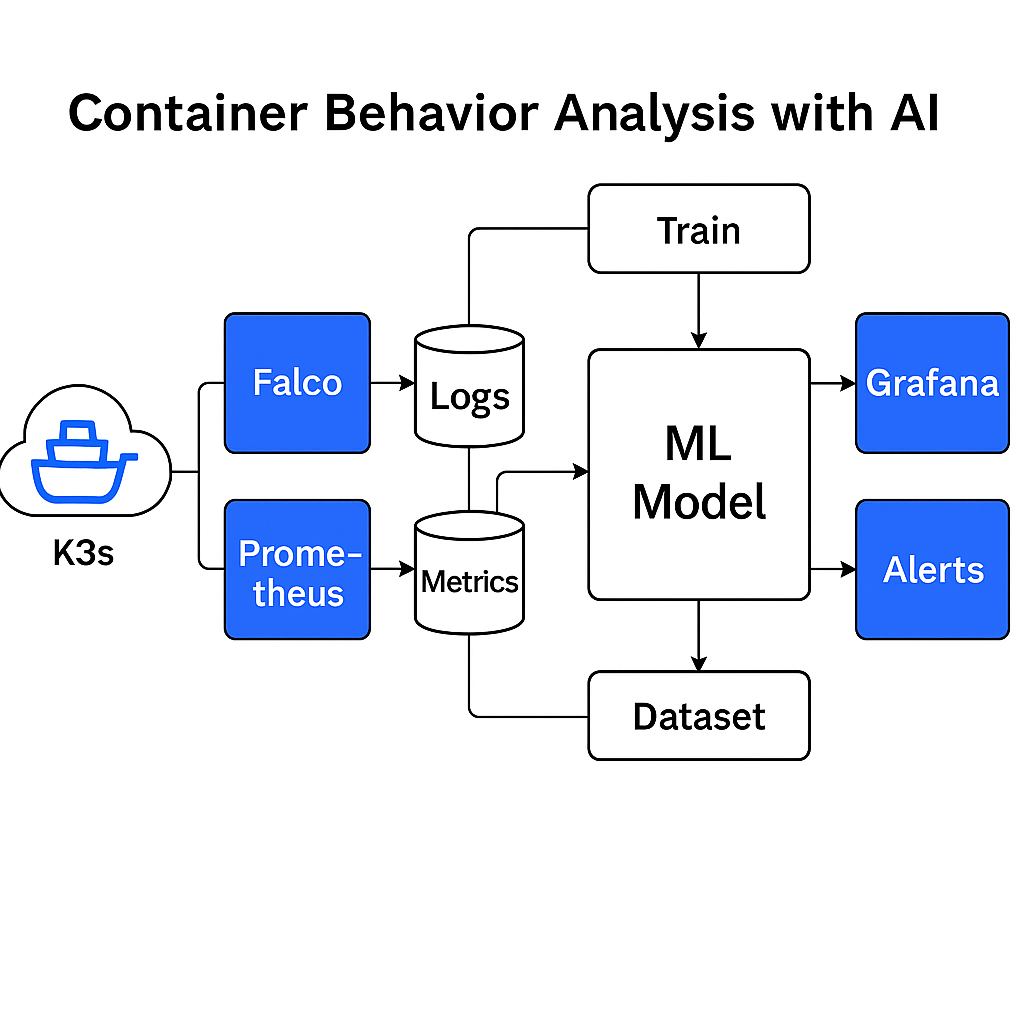
Overview
Learn the normal behavior of containers (e.g., CPU usage, syscalls, network connections) and use AI to detect anomalies that may indicate compromise or misuse.
Components Used
| Component | Purpose |
|---|---|
| K3s | Lightweight Kubernetes cluster |
| KubeSphere | Dashboard & DevOps tools (CI/CD, observability) |
| Falco | Runtime security and syscall monitoring |
| Prometheus | Metrics collection |
| Grafana | Metrics and anomaly visualization |
| Python ML | Training and running AI models for anomaly detection |
Step-by-Step Implementation
1. Deploy Falco to Monitor Runtime Events
Falco monitors system calls made by containers in real time. Add helm repo.Deploy falco with the falcosidekick enabled. The sidekick will allow falco to forwards its logs to loki,
1
2
helm repo add falcosecurity https://falcosecurity.github.io/charts
helm repo update
Deploy falco via helm.
| Setting | Purpose |
|---|---|
| falcoctl.artifact.install.enabled=false | Redundant for eBPF |
| falcoctl.artifact.follow.enabled=false | Causes crashes in K3s/minimal OS |
| falco.http_output.enabled=true | Enables logs to be sent via HTTP |
| falco.http_output.url=”http://falcosidekick.falco:2801” | Set output to Falco pod internal DNS name |
1
2
3
4
5
6
7
8
9
10
11
helm install falco falcosecurity/falco \
--namespace falco --create-namespace \
--set falco.driver.kind=ebpf \
--set falco.ebpf.enabled=true \
--set falco.privileged=true \
--set falcoctl.artifact.install.enabled=false \
--set falcoctl.artifact.follow.enabled=false \
--set falco.http_output.enabled=true \
--set falco.http_output.url="http://falcosidekick.falco:2801" \
--set falco.json_output=true \
--set json_include_output_property=true
Now install the falcosidekick. The sidekick will allow falco to forwards its logs to Loki.
1
2
helm repo add falcosecurity https://falcosecurity.github.io/charts
helm repo update
Install with UI
1
2
3
4
5
6
helm upgrade --install falcosidekick falcosecurity/falcosidekick \
--namespace falco \
--set config.debug=true \
--set service.type=ClusterIP \
--set webui.enabled=true \
--set webui.service.type=NodePort
Run kubectl get svc -n falco falcosidekick-ui to see which port the UI is being forwarded to. You should be able to access the UI at Node_IP_Address:NodePort. A prometheus endpoint can be scrapped at /metrics.